Iphone 4s Ssh Jar
Last week a tethered jailbreak was released for iOS 6 running on the iPhone 4, iPhone 3GS, and iPod touch 4th generation. While it was great to have a jailbreak so soon, the jailbreak didn’t include any GUI tools like Cydia, only SSH and afc2 support were added.
This project now hosts the successor to the original J2SSH API; J2SSH Maverick. This new API was built from the ground up by the original author of J2SSH back in 2003 and has been maintained and available since then exclusively under a commercial license.
This API is now available to the community under the LGPL open source license. The project continues to host both the original API and legacy applications created around it, however these are now considered deprecated and we do not recommend their use in anyway.
This does seem to be the case - the tools execute, device_infos returns some information, useful at least for a partial decryption of a physical image. Is it feasible to patch kernel memory once a jailbroken A5 device is already booted? Or would this require a modification to the Corona payload to apply the new kernel patch along with the others.
Link of MapSource v6.16.3 - Patched on #5 link of language files for Mapsource v6.16.3 Special (Patched) 2.) on #7 MapInstall v3.14.4 Special. Mapsource 6163 patched. Mapsource 6.16.3 - Patched Mapsource 6.16.3 - Patched Changes made from version 6.16.2 to 6.16.3: Fixed some map display issues (22s & 71s labels instead of highway names). Fixed Pedestrian routing. Fixed Pedestrian routing.
I am waiting on some hardware to be able to start looking into this myself. In the meantime, any perspective on how to go about this would be greatly appreciated. Original comment by 0x56.0x6.@gmail.com on 29 Feb 2012 at 4:32.
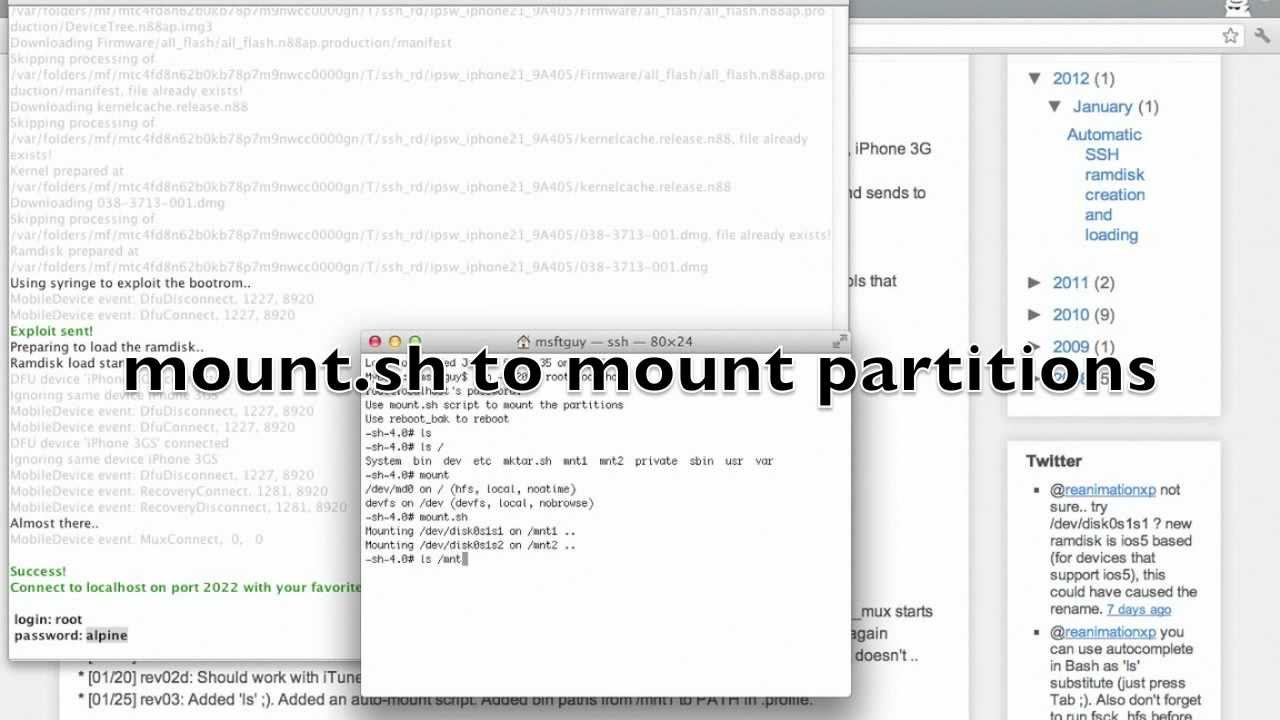
Grapple: First, install OpenSSH on the A5 device through Cydia. Then, use scp or sftp to upload the ramdisk tools (specifically, bruteforce and device_infos; restored_external doesn't matter here) and kernel_patcher (attachment in this issue) to the device. Once the files are uploaded, connect with ssh. Run kernel_patcher to gain access to the crypto engine, then you can run device_infos followed by bruteforce to generate the keys.
I haven't quite figured out pulling an image, as the filesystem is mounted and active while the device is running (I pulled a dd image, but there were some issues with trying to decrypt it, probably because I was still using the phone while the image was running.). That is the general idea of what to do, hope it helps get you started. Simg: Unfortunately, without access to the GID key, the encrypted KBAGs cannot be decrypted. By the time iBoot is finished and passes control to the kernel, the GID key is rendered inaccessible until a reboot of the device. The limera1n exploit allows running unsigned code at a stage in the boot process where the GID key is still accessible. Corona (which Absinthe is used to inject on A5 devices) exploits the kernel, so by the time it takes place, the GID key is inaccessible. Tl;dr KBAG keys will not be available on A5 devices until a limera1n style exploit is discovered:) Original comment by 0x56.0x6.@gmail.com on 9 Mar 2012 at 7:18.
I'm trying to recompile kernel_patcher.c for another purpose, but I can't get it to run on my device. I'm in deep trouble here. Probably amateur problems for you guys. Short story- ipad 2 5.0.1 jb with absinthe. Download new bodyworks 60 crack 2016 download and software free. Wanted to use iUsers but realized after install it was for 4.x and lower. Uninstalled iUsers, caused springboard to crash every respring. Was planning to re-jb with absinthe however unable to jb because 'stash' is found.